- Cybercrimes are now moving from realm of digital to physical world and affecting lives of individuals
- Cybersecurity is only as strong as the weakest link and needs a multi-layered defence
- Banks have to continue to engage in multi-pronged approach with layered security systems to minimise the chances of an intrusion
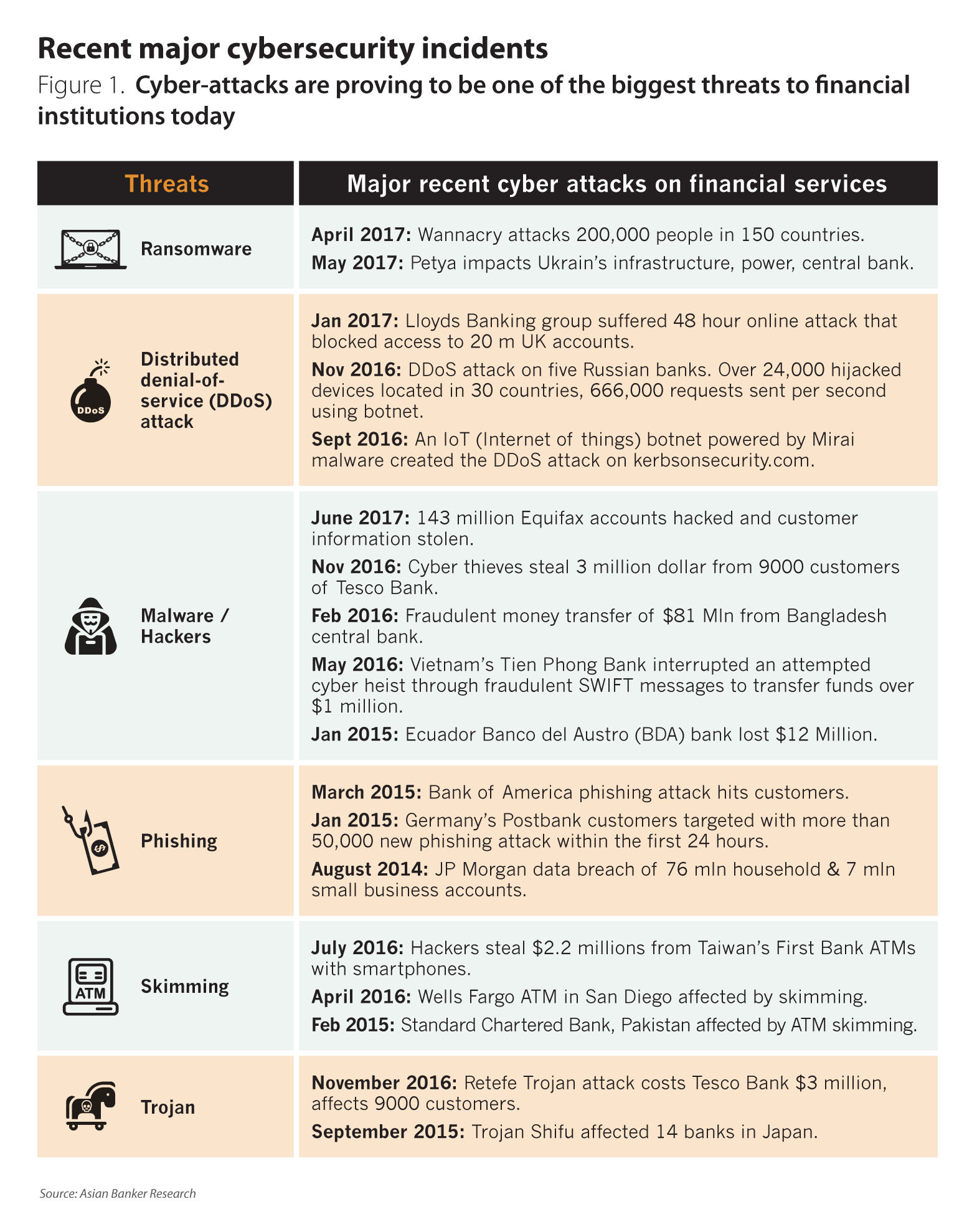
The loss estimated from cybercrime is substantial and rising. The 2016 Internet Crime Report by the Federal Bureau of Investigation showed that the Internet Crime Complaint Centre in the US received a total of 298,728 complaints with reported losses in excess of $1.33 billion in 2016, a rise of 24%. Over last five years the centre has received complaints worth losses of $4.63 billion. Gemalto’s Breach Level Index, a global database of public data breaches, highlighted that 918 data breaches led to 1.9 billion data records compromised worldwide in the first half of 2017, an increase of 164% compared to the last six months of 2016. According to Cybersecurity Ventures, cybercrime will cost most that $6 trillion globally by 2021. There are other varied and alarming reports, yet most experts agree that cybercrimes are often under reported. The nine months of this year has already seen some unprecedented attacks.
Wannacry proved to be the biggest ransomware attack in the history that attacked over 200,000 people in 150 countries while Petya attack had a widespread impact particularly on Ukraine’s infrastructure. In June 2017, 143 million accounts of Equifax, a US-based credit scoring company, were hacked to steal sensitive customer information including customers’ social security numbers, name, address and date of birth, driving licence. Recently, Yahoo admitted that every single account of three billion users was hacked in 2013. The list continues; however, the span and novelty of attacks teaches the financial institutions some important lessons (Figure 2).
Criminals have access to advanced technology and the threat is constantly evolving
In May 2017, a malicious ransomware “WannaCry” spread across corporate and government networks including hospitals and critical infrastructure, paralysing businesses that were unable to access systems and even affecting patient care in the UK. The criminals sought to monetise it through bitcoin. It affected about 200,000 computers, largely the ones that were using the older version of Microsoft’s operating system, until a kill switch was discovered by a researcher. The impact of the attack should have been minimal because Microsoft has already released a patch in March to address the vulnerability yet many had not updated their systems. It highlighted the importance of having the basics right - regular back-up of the systems, system updates, patch management and anti-virus. Interestingly, “WannaCry” spread far utilising an exploit called “EternalBlue”, hacking tools leaked by a group called the Shadow Brokers in April.
“The reality is that criminals are not using ‘off the shelf’ software. Hackers have managed to steal and get access to some of the most advanced and powerful software that was developed by National Security Agency, USA and Wannacry was result of this theft,” said Amar Singh, a cyber security expert, CEO and founder of Cybersecurity Alliance and Chair of Security Group ISACA. There apparently are other NSA exploits that could be potentially used by hackers in future attacks.
“Using these exploits, a hacker can get into one computer to another within the same network or wifi without any user interaction or a phishing email, completely hidden,” pointed Saket Modi, CEO and co-founder at LucideusTech. “The problem with hacking is that you only read about it and not see the impact. The normal human psychology is that it happens to other people,” he added.
“You are dealing with criminals who are going after big money. There are probably many gangs which are trying to shift from traditional crimes such as drugs etc to cybercrime because unlike traditional crimes, there is little risk to criminals’ life in cybercrime. Now with the criminals having the availability of super advanced tools, next years are not going to be easy for the organisations”, pointed Singh. Cybercrimes are now moving from realm of digital to physical world and affecting lives of individuals.
Inflicted by Wannacry, many hospitals were forced to send patients home. A cyber attack on infrastructure can also pose dangers to the lives of citizens, for example Petya impacted Ukraine’s crucial infrastructure including its central bank, airport, metro transport, and even the Chernobyl power plant. In 2015, a German steel plant was adversely impacted by cybersecurity attack, causing the plant to shut down and causing massive damages to the blast furnace.
Cybersecurity is only as strong as the weakest link and needs a multi-layered defence
With constantly evolving digital world and new technologies, security challenges are on the rise. Internet of things (IoT) is predicted to interconnect over 50 billion devices by 2020 through a cloud environment which has its own security challenges.
With artificial intelligence, there is an increasing mediation of human communication with machines. New integrated systems fade the traditional boundaries as the attack surface expands dramatically making effective cybersecurity increasingly complex to deliver. In this dynamic landscape it is important that security people come into the plan at very early design stage.
“There are three categories of actors in cyber-attacks – state sponsored actors, cyber criminals and cyber-hacktivists. They are able to adopt new methods and technology much faster and much better than commercial businesses. If you’re implementing a new technology, engage the security team proactively. Don’t wait until the end of the project to engage the security team and then expect a quick sign-off approval,” commented Theo Nassiokas, director, APAC cybersecurity at Barclays.
Even with best innovation there can be no guarantee of complete security against cyber threats and hence the institutions need to anticipate every attack and need a champion with a security mindset. Through increased mobility, access of internet through smart phones, bring your own devices within the organisations and interconnected devices; it is becoming easier for criminals to get access through one weak link or device. Raising cybersecurity awareness among staff is extremely important as sometimes clicking on one single infected email by an employee could risk a bank’s network.
Organisations need to go beyond traditional perimeter defences. Cybercriminals could exploit user credentials to get access to systems and hence the need to ensure multi-factor authentication across all end and privileged users, cloud and on-premises applications. Besides intrusion prevention measures, authentication measures such as biometrics and education, banks also need to adopt analytics based intelligence-led approach to build cyber resilience.
Institutions need to be constantly vigilant against smart and hidden operatives. “Cybercriminals may bid their time to strike. For example, Carbanak is well known for compromising a bank but they will not damage your system. They will watch, observe and learn from system and they have the patience. In few months they learn how the bank operates, their procedures and then they will repeat same action, so anomalous activity is not detected,” explained Singh.
In case of Bank of Bangladesh attack also, where 81 million dollars were stolen, a malware including spying programme was introduced in the system that led the criminals know how transactions were conducted without being detected. Yet not all attacks are new or more advanced.
“Every attack appears different but modus operandi may be similar. Criminals are lazy and often use strategy that works for other criminals so output may be different but actual method of compromise may be same. It needs scenario-based testing,” commented Singh. He highlighted CBEST as a framework that can guide banks on how to run the security assessment and be proactive.
With a range of attacks and threats in the market today, no one solution fits all. The banks are and have to continue engage in multi-pronged approach with layered security systems and processes in other to minimise the chances of an intrusion. As the attacks become innovative the
question no longer is ‘if’ but ‘when’. “The question often asked is: ‘Are you secure’? But I think that a better question is: ‘Are you prepared to deal with this type of an attack,” opined Singh.
It is not an IT problem but a “business” issue that needs strategic planning of people, process and technology
“If you plan properly you can hack into a system that is not a PC or a computer, for example Supervisory Control and Data Acquisition Systems used by high-tech facilities such as energy companies. Your Fridge or Television can also now be hacked into and used to take unauthorised photographs and recordings of conversations. This is because like so many IoT, they are inherently vulnerable,” said Nassiokas. “It is important to note that there is no cybersecurity, there is only security. It is not the responsibility of just the IT staff in the company, it is everyone’s responsibility,” he added.
“The foundation of a secure organisation has to be the management accepting that cyber risk is a business risk, an information risk and a business issue,” pointed Singh. Technology security risk management needs to begin with business model and organisational risk framework. While information security concerns protection data and information, cyber security goes beyond that towards protecting services which may be non-data related. Some institutions are now focusing on converged security strategy where information risk management, cyber security, physical security and resilience are placed under one chief security officer. This converged strategy connects and allows stepping back and seeing the big picture.
“Different organisational structures for security will work for different organisations as there is no one size that fits all. However, one common denominator is that the CEO simply has to understand the issue and be supportive of everyone below him with regards to all risks and security issues, irrespective of the structure,” Nassiokas pointed.
Banks need to involve security at early stage and also ensure that board is aware of the cyber risks. They would need scenario analysis with technical team to identify what attacks are technically possible and need to analyse the potential losses with the business teams. Armed with this information the institutions can reach for a decision from the board, explaining the risks and steps needed to mitigate the risk. “The problem is that security is often practiced in different silos which prevent standardisation or real understanding of the risk level,” noted Dante Fuentes, chief compliance officer, Security Bank Corporation.
The siloed approach will not be effective and the institutions need to develop a holistic IT risk management framework with senior management and board oversight.
“Institutions need to have an effective policy that is tailored specific to the organisation. It is more that technical infrastructure, it needs to educate employees and it should be one that employees are fully aware and familiar with, it should include everyone in the organisation. When it comes to IT security policies, change is inevitable. No matter how well you design IT security policy, the time will come that it no longer balances the business requirement with the required security measures necessary to protect the infrastructure and the data against the evolving landscape,” Fuentes pointed.
How are regulators tightening their controls?
While the onus has been on institutions to manage their security, there are also heightened concerns and advisories from banking regulators to strengthen measures against cyber-threats.Regulators are increasingly advising the institutions to develop a cyber-resilient framework with clear policies and top management oversight (Figure 2). For instance, New York Department of Financial Services requires regulated financial institutions to establish a cybersecurity program, adopt a written cybersecurity policy, designate a chief information security officer responsible for implementing, overseeing and enforcing its new program and policy and an ongoing reporting system for cybersecurity events.
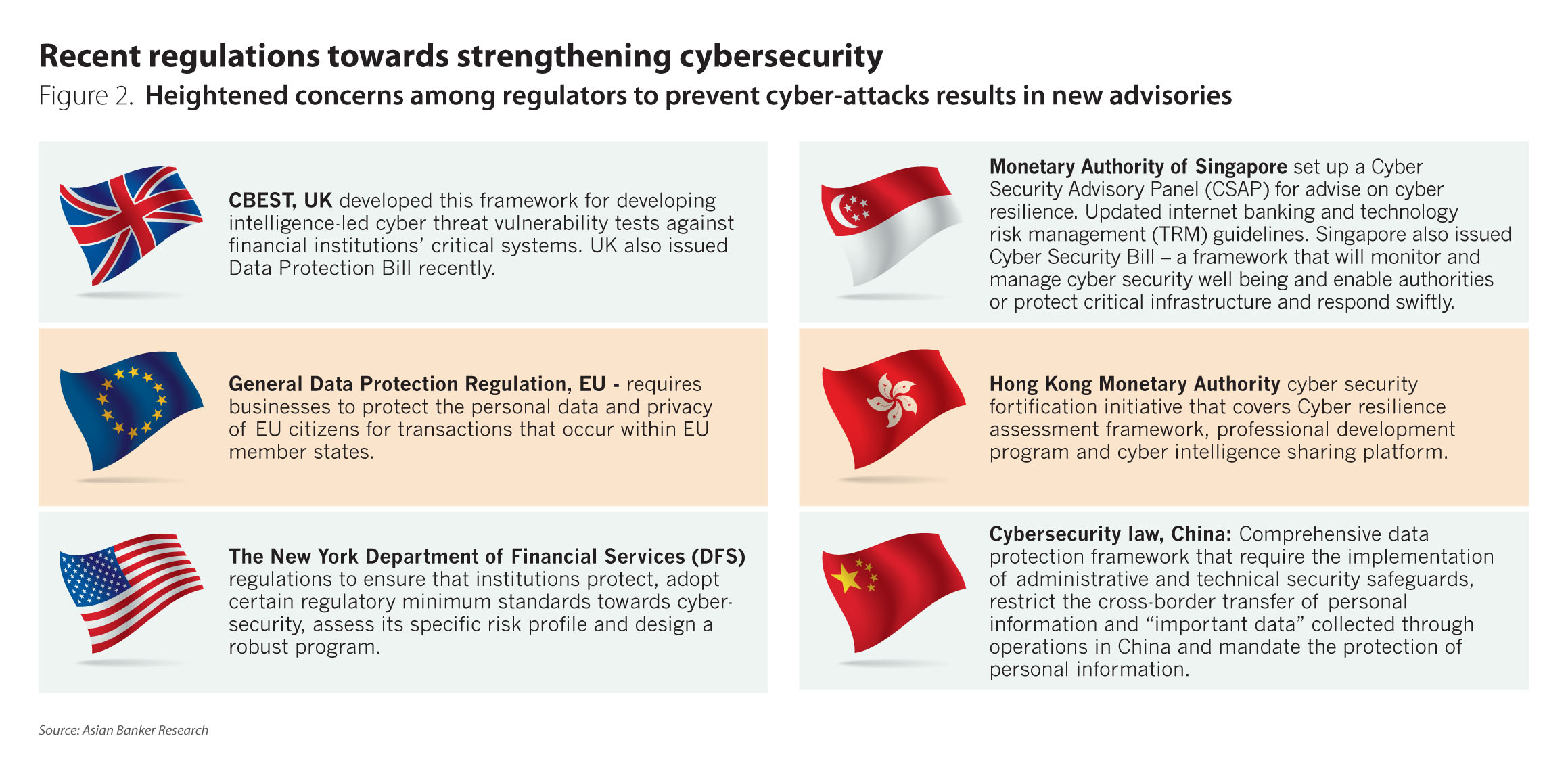
The international nature of cybersecurity threats requires greater information sharing. Hong Kong, in its cybersecurity fortification initiative, incorporates an element of effective infrastructure for sharing intelligence in which all banks are expected to participate. Building a strong knowledge base and haring of knowledge and experiences across the banking sector can allow faster and more effective response to these attacks. A lot of banks and governments are actively engaging in intelligence sharing which can prove to be an effective way to reduce risk.
Data and information protection regulations are becoming increasingly stringent. General Data Protection Regulation, which comes into force in May 2018, will have ramifications globally for all companies with operations in EU. Through this EU intends to strengthen data protection for all individuals and has proposed severe fines for non-compliance. A cybersecurity advisor panel by Monetary Authority of Singapore stressed the need for realistic penetration tests including “red teaming” (a team of ethical hackers to test the weakness in the systems). Yet another initiative, CBEST by UK Financial authorities is a common framework that delivers a controlled, bespoke, intelligence-led penetration test against financial institutions’ critical systems.
As threats rise, cybersecurity regulations will continue to expand and new regulations will emerge as digitisation brings new cyber risks to forefront. With cybercriminals constantly refining their techniques, there is an urgent need for institutions to implement an enterprise-wide cyber-resilient framework that is multi-layered and tailored to their unique requirements and risks of the institutions whilst meeting the demands of constantly changing security needs.

































