Addressing cyber threats continues to be an uphill battle. In 2022, cybercrime complaints to the FBI’s Internet Crime Complaint Center reached over $10.3 billion, a 49% increase from the previous year. The UK’s National Cyber Security Center reported 2.7 million cyber-related fraud incidents in one year. Singapore Police noted a 25.2% rise in scam and cybercrime cases, amounting to $660.7 million in losses.
Geopolitical tensions have fueled state-sponsored attacks while organised cyber criminals adopt advanced technologies. Several security agencies anticipate further increase in threat as cybercrime-as-a-service improves access to malicious tools and lowers entry barriers.
A survey by TABInsights across 250 financial institutions (FI) in Asia validates this with 74% of respondents noting an increase in scams, 69% in money laundering, and 64% in malware in 2022.
Regulations become stringent and expansive
Regulators worldwide are responding by intensifying monitoring and issuing new guidelines to enhance data and cyber security. FI must enforce robust measures to prevent, detect, and respond to fraud, with regulators holding them accountable for any lapses. Non-compliance and inadequate protection often result in hefty fines. For instance, in Singapore, OCBC reported losses of SGD 13.7 million ($10.2 million) from SMS phishing scams, following which the Monetary Authority of Singapore directed it to increase its operational risk capital by SGD 330 million ($240 million). It also tightened cyber security guidelines including a loss-sharing framework for FI.
Regulations are evolving rapidly across Asia. In 2022, Malaysia mandated additional security measures for FI to safeguard against online scams and strengthened collaboration with banks and law enforcement agencies. The Philippines amended regulations for IT risk management, cyber security, and fraud management and asked FI to integrate fraud and anti-money laundering (AML) systems and have a real-time fraud monitoring system. Thailand granted banks more power to block suspicious transactions and encouraged greater information sharing among FI, businesses, and telecom companies.
Meanwhile, data residency laws prevail in several Asia Pacific (APAC) countries and data privacy regulations have expanded. Several countries like Australia, Singapore, China, Thailand, Indonesia and Sri Lanka already have comprehensive privacy laws in place, while India and Vietnam are now implementing them.
Regulators emphasise the importance of robust technology-risk governance, IT and cyber resilience, and addressing third-party risks. FI are urged to prioritise customer education, authentication, fraud surveillance, customer handling, and recovery, alongside equitable loss-sharing.

Institutions need holistic information security
Real-time digital transactions, mobile devices and remote systems open new attack opportunities. Potential threats emerge with interconnected systems, ecosystem partnerships, and third-party reliance. Recent attacks demonstrate the gaps and the urgency to plan strategically for holistic and comprehensive information security.
Last year, Australian telecom company Optus lost 9.8 million customers’ data due to an unprotected application programming interface that lacked user authentication security. In another breach, Latitude Money saw the theft of 7.9 million driver’s license details, alongside 6.1 million records, of which 94% were from before 2013. These breaches in Australia show lapses in data security and governance.
Data security and governance: Virag Thakkar, regional information security officer at Allianz Partner explains: “Organisations have traditionally been storing a lot of data without having the need to. Given the spate of data breach incidents, data governance becomes very important. Firstly, organisations need to assess whether they need so much data. Secondly, they must follow privacy impact assessments from information, cyber security posture and privacy risk.” The breach in Latitude Money happened due to lapses by its outsourcing partner. In some incidents, attackers use fake telecom base stations to exploit vulnerabilities of older telecom networks to steal data. These incidents accentuate the need for stronger third-party network and system security reviews and controls.
Insurance company Medibank lost 9.7 million customers’ data as criminals used a stolen credential from a third-party IT service provider and accessed systems through a misconfigured firewall lacking a digital security certificate. Given the weakness in the company’s security, the regulator penalised them with an extra capital requirement of AUD 250 million ($167 million). Such incidents stress the importance of multifactor authentication and stronger access controls.
Zero trust framework: Pepijn Kok, chief information security officer (CISO) and head of cyber security at Advanced Info Services remarked: “In my experience, 50% of the machines involved in cyber security incidents are not in any register—no patches, antivirus and monitoring. It is very important to know what is going on in your network. It is nearly impossible to create a safe environment. We are always at the back foot as the protectors, especially with the increasing zero-day attacks and attackers using AI [artificial intelligence] and automated tools.”
Zero-day attacks refer to attacks that exploit vulnerabilities before developers become aware of it or have a chance to address it. These attacks are especially serious as there is no defense in place against these, no patches or anti-virus signatures, and they can lead to extensive damage.
Kok explained: “The zero-trust principles framework is important. Every single time of the day you should assume that there is someone in your network who shouldn’t be there, and you should be looking for them. And once you do, you need to take care of that access.”
The zero-trust framework assumes no implicit trust and focuses on protecting resources and data regardless of user location. It emphasises strict access control and user authentication across the network.
Increase reliance on AI: Bots are being used in attacks, and generative AI-based tools such as WormGPT, a malicious chatbot to aid online criminals are being released. On the other hand, FI are also expanding the use of machine learning (ML) in faster risk detection such as anomaly detection, uncovering network vulnerabilities, commonalities to spot attacks, behaviour analytics and others.
The survey by TABInsights shows that a significant 47% of FI have already adopted ML tools, while 37% are now beginning to use them.
Banks increasingly use proactive defence using AI-based intelligent risk control, covering hundreds of risk labels, ML models, knowledge graphs and privacy computing through federated learning to address fraud and cyberattack in real-time.
Several banks use behavioural biometrics, location analysis, and device fingerprinting to determine user identity and prevent fraud. One bank in China uses customer identity, transactions and risk information, adopting ML and graph algorithms to monitor accounts across multiple dimensions, identify potential risks, extract potential criminal gangs, and customer risk timelines, and help businesses to manage risks in real-time.
While ML models can be used to spot known threats and vulnerabilities, they are often ineffective against zero-day attacks. Banks are implementing intrusion detection systems and behaviour-based analysis to address these. They must have continual risk assessment, engage external agencies and ethical hack teams to identify vulnerabilities in defence and have robust scenario planning. Alongside this, having stronger threat intelligence mechanisms across the industry can also help avert these attacks.
Plan for human errors: “The technology will mature, but the problem lies usually between the chair and the computer—the human beings,” commented Suresh Ramasamy, CISO at Center for Advanced Computing and Telecommunications (CACT).
Kok confirms this, saying: “80% of the incidents occur due to human error. Many of these include well-willing administrators that used the wrong version of the software or forgot to get rid of default accounts on an internet-facing server which gets compromised.”
FI must ensure basic cyber hygiene including patch management, and have privileged access controls ensuring data access is limited to only where needed. Institutions must have regularly updated security policies, monitor employees and strengthen customer and user education.
Be prepared for incident response: Despite measures, an organisation can never be sure of complete security. Ramasamy added: “If I have a malicious threat actor running in my organisation, do I have enough tripwires in the organisation to be able to detect them? But assuming a breach does happen, how prepared am I to handle that situation? These are some of the areas that FI must be prepared for.” Well-planned incident response is critical to managing the damage, both monetary and reputational. The speed of response and external communication will impact the public reaction to the attack.
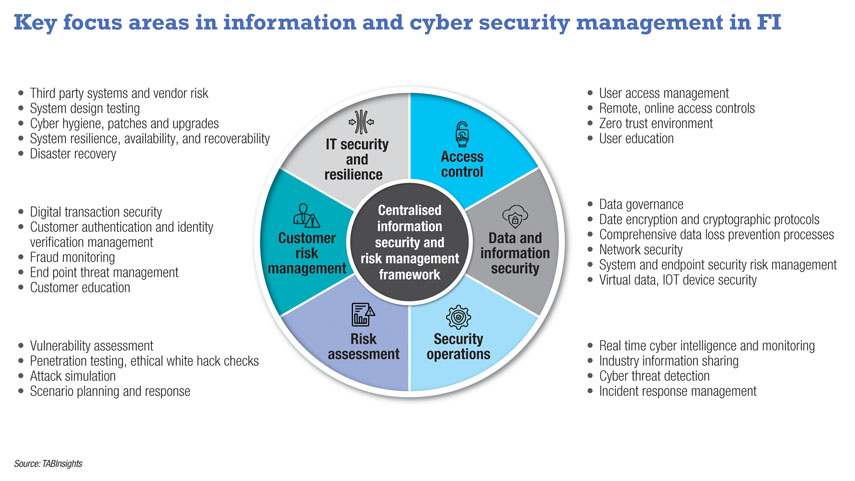
Integrated centralised approach: FI must have centralised strategic risk management with holistic oversight of policies, functions, responsibilities and processes. It is crucial to integrate data, technology and processes across siloes in the organisation, alongside multilayered controls and fraud prevention technology systems. Integrated risk insights across functions such as AML, fraud, compliance and cyber security can enable faster and timely detection. In addition, data sharing across the industry can play a key role in addressing fraud.
The threat landscape and regulatory requirements will continue to constantly evolve. It is crucial for FI to strategically adapt and enhance security practices to stay ahead, and yet prepare for the worst.